What would you say if a competitor came up to you in a coffee shop and asked for the names of your three biggest customers? You could say “Get lost,” “Take a hike,” or “Sorry, that’s proprietary information.” After all, there’s no reason to divulge that kind of hard-earned information about your business.
Today, almost every business relies on proprietary information to some degree, from Coca-Cola’s legendary secret beverage formula to your monthly sales reports or the wealth of data stored in your customer relationship management (CRM) system. So, take a moment to think about the most important information in your business – the “crown jewels” of your operations that you need to keep out of the hands of your competitors.
Your proprietary information could include trade secrets, production methods, marketing strategies, software applications and financial data. After all, you don’t want everyone knowing how your sales, profits or customer base change from year to year. Perhaps you’ve developed a proprietary machine tool, sealant or coating for a manufacturing operation, or a new algorithm for delivering targeted ads to your customers on social media. These are products and processes that belong to your business and need to be protected to maintain a competitive advantage.


Other types of proprietary information include product specifications, chemical formulas and cooking recipes. In many cases, these trade secrets provide the foundation for a startup business or an extension of a current product line. For example, the owners of a key lime pie company started as a roadside stand selling the tangy desserts made from local Florida limes. They opened a brick-and-mortar store but were unable to turn a profit.
When the owners turned to Marcus Lemonis for help, he realized that one of the factors holding the business back was using generic, pre-made ingredients to produce a larger volume of pies, rather than the original homemade process that attracted customers when they started out. Marcus helped the owners refine their processes for mass producing handmade crusts with fresh key lime filling, and they began selling their signature pies using a new proprietary recipe. Since then, the company’s sales have taken off, and the pies have won numerous culinary awards, including “Best Pie in Florida” from USA Today.
Why is Proprietary Information Important?
Proprietary information is a legal concept that refers to the rights you hold as a business owner or “proprietor.” It typically refers to confidential information that gives you a competitive advantage in regard to your people, processes and products.

As a general rule, proprietary information refers to material held within your organization that would not be readily available to the public.
For instance, if you used an online search engine to find 25 potential customers for your products or services, the resulting list would probably not be considered confidential. After all, anyone else could do the same thing, including your competitors. On the other hand, if you have taken the time to compile detailed notes about your 25 top customers and keep the data in your CRM, that material would almost certainly be considered proprietary.
There are many ways you can use proprietary information to attract new customers, increase revenue or grow your market share.
For instance, you could draw on your customer database to launch an advertising program targeted at similar prospects. You could adjust your product price points up or down depending on confidential information from your suppliers, or capitalize on social media feedback to improve your services.

Of course, if you have developed a secret sauce, a unique blend of beverage flavors or a new food preparation method, you could build an entire business around your trade secrets. For the co-owners of a BBQ restaurant in Kentucky, the creative use of proprietary information led to a wildly successful new product line. Several years ago, Marcus met with the owners to see how they could grow their small family business. He looked at the restaurant’s proprietary recipes for barbecue sauce and suggested selling bottled sauces online as well as in their store. The result was a new revenue stream from a relatively small investment.

There are plenty of other creative strategies you could consider to help grow your business. For example, you could offer a one-time use of your proprietary customer list to a charitable organization in your community in order to attract a larger audience to a local fundraising event. This can be a true win-win relationship that allows you to maintain control of information, while building a new partnership, meeting other business and civic leaders, and generating favorable publicity as a sponsor of a worthy cause.

Protecting Proprietary Information
Because your proprietary information has value, it needs to be protected from a variety of internal and external threats. That typically requires a multi-layered defense strategy tailored to your business’s specific operations. Today, threats can come from almost anywhere, so you need to pay attention to your people and processes and shore up any vulnerable areas.
The first step is to identify your trade secrets, as well as any other information you need to keep confidential. That will help you determine your security priorities. Depending on the nature of that proprietary information, you can then take appropriate measures, such as the following.
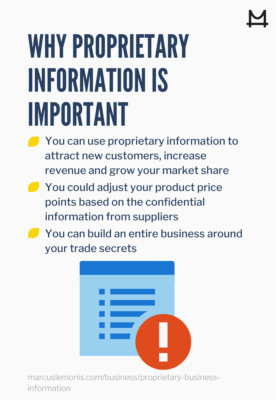
- Cybersecurity. You should invest in a strong cybersecurity program to protect the most valuable proprietary information from hackers. That might mean installing strong firewalls and authentication procedures, or relying on a cloud-services provider who can guard against the ever-changing cybersecurity threats. You should also be sure your employees understand and follow your security protocols. Few things are more damaging to a business than a criminal breaking into your system and stealing trade secrets, personal customer data or other proprietary information.

- Access control. Depending on your business, you may be able to limit physical access to your facility to employees and approved visitors. A data center or executive office suite may have even stricter access controls. Software applications, such as CRM programs, can also be adjusted to prevent employee access to confidential data. A salesperson, for example, might have full access to information about her own customers, but not to customers of other representatives.
- Internal security. Your laboratories, production areas, conference rooms and executive offices should be kept secure to guard against leaks of confidential information. That might mean automatic door locks when someone exits the area, putting tinted glass on windows, or adding security features to communications devices in these locations to prevent unauthorized recordings.

- Non-disclosure agreements. Many businesses use written non-disclosure agreements (NDAs) to keep employees from revealing proprietary information while working for the organization. Suppliers, outside sales representatives and other business partners can also be required to sign NDAs before accessing your business’s data.
- Non-compete clauses. An employment agreement can also contain a non-compete clause that prevents a former employee from using proprietary information in a competitive role. For instance, you wouldn’t want a sales manager to leave your company on a Friday, join your top competitor over the weekend, and start calling your best accounts on Monday.
You should be aware that many of these protective steps require specialized knowledge, such as expertise in network security tools or access control protocols. An experienced attorney should be engaged to help you draft NDAs and non-compete documents that comply with applicable state and federal regulations. After all, you don’t want to go into court expecting to be compensated for the loss of proprietary information only to find that your NDA or non-compete was invalid right from the start.

Don't Let Your Guard Down
It’s not enough to put a series of safeguards in place and get back to your daily business activities. That’s because your proprietary information is not a one-and-done bundle of secrets tucked away in a safe deposit box.

That confidential data is constantly changing with the acquisition of new customers, the launch of a new product or service line or an entry into new markets. Cybercriminals are constantly looking for new ways to attack your confidential database and extract your secrets. Meanwhile, the laws regarding NDAs and other confidential disclosures continue to evolve, and documents prepared in the past might need to be updated.
Therefore, you need to stay focused on securing your proprietary information and monitor potential threats to reduce the risk of a costly unexpected surprise.
- What proprietary information does your business currently have?
- How do you plan on protecting your proprietary information?
Nieds, M. (2015, October 21). 5 tips to protect your proprietary information. Retrieved from www.swflbusinessandipblog.com/2015/10/5-tips-to-protect-your-proprietary-information/
Upcounsel.com. (n.d.). What is proprietary: everything you need to know. Retrieved from https://www.upcounsel.com/what-is-proprietary#:~:text=Proprietary%20information%20is%20important%2C%20possibly,or%20maker%20may%20be%20proprietary